#security
236 articles found
Latest
What Is a Rekt Test and How to Pass It?
 The Rekt Test is a specialized questionnaire developed by a team of web3 security experts, spearheaded by Dan Guido, the CEO of Trail of Bits. Trail of Bits is a cybersecurity company whose clientele includes notable organizations like Facebook and the Pentagon's Defense Advanced Research Projects Agency (DARPA).
The Rekt Test is a specialized questionnaire developed by a team of web3 security experts, spearheaded by Dan Guido, the CEO of Trail of Bits. Trail of Bits is a cybersecurity company whose clientele includes notable organizations like Facebook and the Pentagon's Defense Advanced Research Projects Agency (DARPA).  According to a study by Salesforce, approximately 74% of customers are concerned about the unethical use of new technologies. That said, only 57% trust companies' statements on this matter.
Openness to AI is also problematic and has steadily declined over eight months, from 65% to 51%. Customers' primary concerns revolve around security, control, and ethics:
A clear understanding of where artificial intelligence is being applied (as indicated by 89% of respondents).
Verification of AI-generated outcomes (80%).
Bias in the AI-produced results (63%).
Furthermore, 68% of the respondents believe that artificial intelligence amplifies the significance of trust in companies and heightens the responsibility brands owe to their customers.
According to a study by Salesforce, approximately 74% of customers are concerned about the unethical use of new technologies. That said, only 57% trust companies' statements on this matter.
Openness to AI is also problematic and has steadily declined over eight months, from 65% to 51%. Customers' primary concerns revolve around security, control, and ethics:
A clear understanding of where artificial intelligence is being applied (as indicated by 89% of respondents).
Verification of AI-generated outcomes (80%).
Bias in the AI-produced results (63%).
Furthermore, 68% of the respondents believe that artificial intelligence amplifies the significance of trust in companies and heightens the responsibility brands owe to their customers.  Atomic Wallet has landed in legal hot waters. This development comes after a hacking event that wiped out more than $100 million.
The claimants assert that the developers neither informed the users about the security vulnerability nor contacted law enforcement after the breach.
Many prosperous investors, some having affiliations with Russia, are included in the court case.
Atomic Wallet has landed in legal hot waters. This development comes after a hacking event that wiped out more than $100 million.
The claimants assert that the developers neither informed the users about the security vulnerability nor contacted law enforcement after the breach.
Many prosperous investors, some having affiliations with Russia, are included in the court case.  After detecting phishing attempts, Terra (LUNA) has temporarily frozen its primary domain, Terra․money. The company's directive? Avoid sites with this domain until they say otherwise.
While the team has ramped up protection for the Station Wallet, a word of caution: avoid the desktop and mobile apps for a bit. But if you're a fan of the Station Chrome extension, the latest version is good to go.
After detecting phishing attempts, Terra (LUNA) has temporarily frozen its primary domain, Terra․money. The company's directive? Avoid sites with this domain until they say otherwise.
While the team has ramped up protection for the Station Wallet, a word of caution: avoid the desktop and mobile apps for a bit. But if you're a fan of the Station Chrome extension, the latest version is good to go.  The Exactly Protocol has suffered a hacking attack. Running on the Optimism blockchain, this lending DeFi platform was targeted by malefactors who stole over 4300 ETH, totaling approximately $7.3 million.
Both BlockSec and Beosin security agencies have corroborated the theft. The hackers reportedly found and exploited a weak point in the platform's smart contracts, although the finer details are still under wraps.
UPD: The team at Exactly Protocol would declare a $700,000 reward for any leads on the hacker, should they not receive a response from the malefactor by the end of August 22nd.
"You can return the funds, minus a 10% fee to you, without worries about us coming after you," the Exactly team conveyed in their message.
The Exactly Protocol has suffered a hacking attack. Running on the Optimism blockchain, this lending DeFi platform was targeted by malefactors who stole over 4300 ETH, totaling approximately $7.3 million.
Both BlockSec and Beosin security agencies have corroborated the theft. The hackers reportedly found and exploited a weak point in the platform's smart contracts, although the finer details are still under wraps.
UPD: The team at Exactly Protocol would declare a $700,000 reward for any leads on the hacker, should they not receive a response from the malefactor by the end of August 22nd.
"You can return the funds, minus a 10% fee to you, without worries about us coming after you," the Exactly team conveyed in their message.  House Democrats have initiated a working group dedicated to artificial intelligence (AI) with the aim to craft legislation surrounding this tech.
The group, chaired by Representative Derek Kilmer, will explore leveraging AI for growth while ensuring job security for those impacted by AI advancements.
A primary concern is the rise of AI-generated misinformation, especially deepfakes.
House Democrats have initiated a working group dedicated to artificial intelligence (AI) with the aim to craft legislation surrounding this tech.
The group, chaired by Representative Derek Kilmer, will explore leveraging AI for growth while ensuring job security for those impacted by AI advancements.
A primary concern is the rise of AI-generated misinformation, especially deepfakes.  China's provisional AI guidelines, termed "Generative AI Measures," take effect today. Among the 24 measures, AI service platforms must register and undergo security reviews before public launch.
AI-generated content will need labels, and data must come from legitimate sources respecting intellectual property and user privacy. Service providers are accountable for content on their platforms.
China's provisional AI guidelines, termed "Generative AI Measures," take effect today. Among the 24 measures, AI service platforms must register and undergo security reviews before public launch.
AI-generated content will need labels, and data must come from legitimate sources respecting intellectual property and user privacy. Service providers are accountable for content on their platforms. 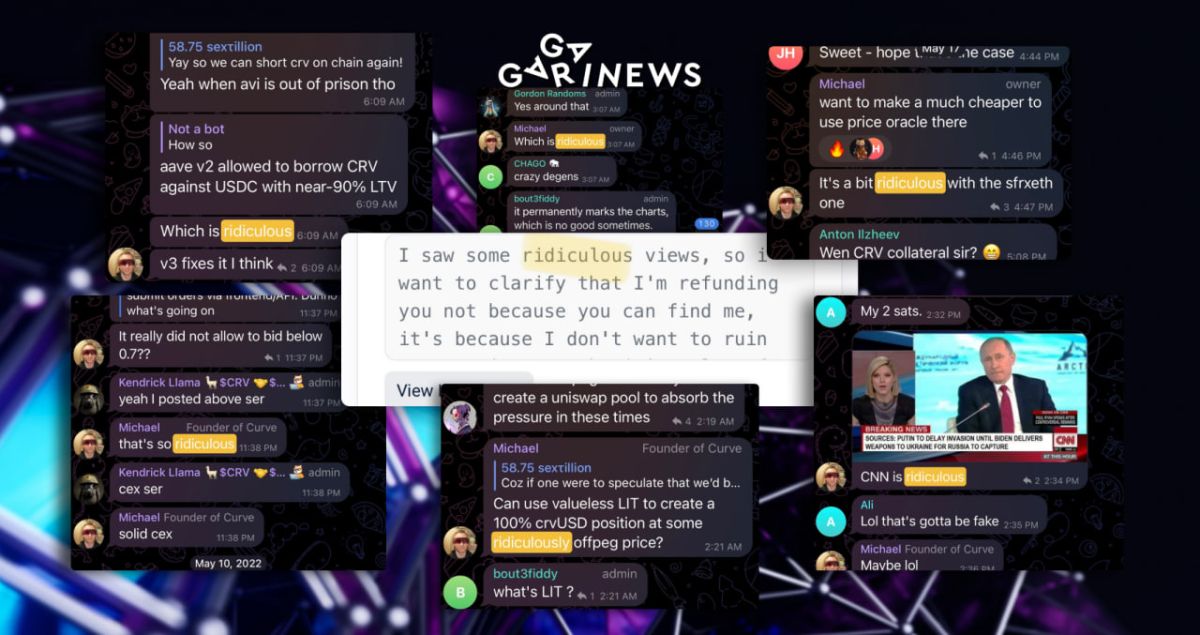 A Twitter user speculates that the Curve founder may be linked to the platform exploit based on a peculiar word choice. The hacker referred to users' reactions to the recent security breach as “ridiculous,” a term frequently used by Michael Egorov.
Additionally, concerns arise over Curve founder’s collateralized loans, with potential liquidation just weeks away.
The coincidence of “ridiculous” being mentioned around 20 times in the tweet makes this theory intriguing.
Furthermore, despite the deadline for fund reimbursement passing last night, the hacker has yet to return all stolen assets from the pools.
Curve Finance is offering a $1.85 million reward for anyone who can unmask the hacker.
A Twitter user speculates that the Curve founder may be linked to the platform exploit based on a peculiar word choice. The hacker referred to users' reactions to the recent security breach as “ridiculous,” a term frequently used by Michael Egorov.
Additionally, concerns arise over Curve founder’s collateralized loans, with potential liquidation just weeks away.
The coincidence of “ridiculous” being mentioned around 20 times in the tweet makes this theory intriguing.
Furthermore, despite the deadline for fund reimbursement passing last night, the hacker has yet to return all stolen assets from the pools.
Curve Finance is offering a $1.85 million reward for anyone who can unmask the hacker. Holochain: Revolutionizing dApp Creation Without Blockchain
 Holochain represents a revolutionary software concept. It serves as an open-source foundational platform engineered for building decentralized applications, commonly known as dApps. Holochain promises security and robustness, operating without the need for centralized servers or blockchain technology, but instead harnessing the power of cryptographic protocols and cloud hosting.
Holochain represents a revolutionary software concept. It serves as an open-source foundational platform engineered for building decentralized applications, commonly known as dApps. Holochain promises security and robustness, operating without the need for centralized servers or blockchain technology, but instead harnessing the power of cryptographic protocols and cloud hosting.  Hackers managed to drain 6000 ETH, 3.9 million USDT, 1.1 million USDC, and 900,000 DAI from the company's address.
Tongue-in-cheek, one might say Drake was responsible for the audit.
UPD: Hacken has disclosed that an initial cyber theft of $20.69 million was executed on the Ethereum network, which was followed by subsequent heist amounting to $25.6 million across the BSC and Polygon networks.
The project's team has not yet commented on the breach.
The only information available is a Telegram channel update, indicating technical maintenance for the withdrawal of ETH, USDT, and ERC20 tokens.
Hackers managed to drain 6000 ETH, 3.9 million USDT, 1.1 million USDC, and 900,000 DAI from the company's address.
Tongue-in-cheek, one might say Drake was responsible for the audit.
UPD: Hacken has disclosed that an initial cyber theft of $20.69 million was executed on the Ethereum network, which was followed by subsequent heist amounting to $25.6 million across the BSC and Polygon networks.
The project's team has not yet commented on the breach.
The only information available is a Telegram channel update, indicating technical maintenance for the withdrawal of ETH, USDT, and ERC20 tokens.  Quantstamp, a blockchain security firm, has introduced the Economic Exploit Analysis tool designed to detect potential flash loan attack vulnerabilities in smart contracts.
While it can analyze multiple contracts from various DeFi protocols, some manual adjustments are needed for specific protocols.
Flash loan attacks, which have drained about $200 million in the Euler Finance exploit alone, are a growing concern in DeFi.
Quantstamp, a blockchain security firm, has introduced the Economic Exploit Analysis tool designed to detect potential flash loan attack vulnerabilities in smart contracts.
While it can analyze multiple contracts from various DeFi protocols, some manual adjustments are needed for specific protocols.
Flash loan attacks, which have drained about $200 million in the Euler Finance exploit alone, are a growing concern in DeFi.  Security company PeckShield has issued a warning to users about a phishing attack conducted by a scammer who has stolen over $675,000 in the past five days. He exploits USDT token permissions. Users are therefore advised to promptly verify and revoke any suspicious accesses to safeguard their assets.
Security company PeckShield has issued a warning to users about a phishing attack conducted by a scammer who has stolen over $675,000 in the past five days. He exploits USDT token permissions. Users are therefore advised to promptly verify and revoke any suspicious accesses to safeguard their assets.  A significant security vulnerability has been identified in the WinRAR utility, potentially allowing threat actors to execute remote code on Windows systems. Dubbed CVE-2023-40477, this flaw arises from improper validation during recovery volume processing. To take advantage of this, users would need to be tricked into visiting a malicious webpage or opening a compromised archive file. The flaw, discovered by a researcher named goodbyeselene, was reported on June 8, 2023, and addressed in WinRAR 6.23 on August 2, 2023. Users are urged to update to the latest version for protection.
A significant security vulnerability has been identified in the WinRAR utility, potentially allowing threat actors to execute remote code on Windows systems. Dubbed CVE-2023-40477, this flaw arises from improper validation during recovery volume processing. To take advantage of this, users would need to be tricked into visiting a malicious webpage or opening a compromised archive file. The flaw, discovered by a researcher named goodbyeselene, was reported on June 8, 2023, and addressed in WinRAR 6.23 on August 2, 2023. Users are urged to update to the latest version for protection.  Crypto miners in the U.S. have initiated the Digital Energy Council to lobby for miner-friendly policies amidst ongoing crypto regulation debates.
The council aims to advocate for sustainable energy development, grid resilience, U.S. competitiveness, and national security.
This move comes as President Joe Biden's administration proposes a 30% excise tax on mining operations, citing societal harms. Additionally, Democratic lawmakers criticize miners for environmental concerns.
Crypto miners in the U.S. have initiated the Digital Energy Council to lobby for miner-friendly policies amidst ongoing crypto regulation debates.
The council aims to advocate for sustainable energy development, grid resilience, U.S. competitiveness, and national security.
This move comes as President Joe Biden's administration proposes a 30% excise tax on mining operations, citing societal harms. Additionally, Democratic lawmakers criticize miners for environmental concerns.  US District Judge Analisa Torres in New York had previously indicated that XRP sales to sophisticated investors fulfilled the criteria for an investment contract under federal securities law
However, this characterization didn’t extend to programmatic investors, which pertains to the general public buying crypto through exchanges.
US District Judge Analisa Torres in New York had previously indicated that XRP sales to sophisticated investors fulfilled the criteria for an investment contract under federal securities law
However, this characterization didn’t extend to programmatic investors, which pertains to the general public buying crypto through exchanges.  The company's developers are gearing up to release JavaScript libraries tailored to facilitate the transmission of commands and signals to mining hardware.
Tether CTO Paolo Ardoino confirmed his direct involvement in the coding process, asserting that this new development will bolster both performance and security.
The company's developers are gearing up to release JavaScript libraries tailored to facilitate the transmission of commands and signals to mining hardware.
Tether CTO Paolo Ardoino confirmed his direct involvement in the coding process, asserting that this new development will bolster both performance and security. Evgeny Gaevoy: The CEO of Wintermute and Liquidity Provider
 Last year's turbulence in the crypto market, which was marked by cyberattacks and growing uncertainty around the security of centralized platforms, has prompted a shift towards the OTC market. Wintermute CEO Evgeny Gaevoy believes that traders are now increasingly seeking alternative methods for trading and protecting their assets.
Last year's turbulence in the crypto market, which was marked by cyberattacks and growing uncertainty around the security of centralized platforms, has prompted a shift towards the OTC market. Wintermute CEO Evgeny Gaevoy believes that traders are now increasingly seeking alternative methods for trading and protecting their assets. 

