Wallet drained via fake Uniswap ad, founder renews warning
A fresh wave of fake search ads impersonating Uniswap has resurfaced in February 2026, after a trader said a single click on a sponsored link led to their wallet being drained of a mid-six-figure sum, prompting Uniswap founder Hayden Adams to renew warnings that “scam ads keep returning” despite years of reports.
Adams’ comments came after an X user posting under the name “Ika” described losing their “entire net worth” after landing on what appeared to be an official Uniswap result at the top of a Google search and connecting a wallet to a cloned interface. The user later framed the incident as the end result of compounding mistakes rather than a random event.
The incident highlights how scammers are buying ads against branded keywords such as “Uniswap,” pushing fraudulent domains to the top of search results where they can look legitimate at a glance. Once a victim connects a wallet and approves a transaction or signature request, the attacker can trigger approvals or transfers that empty balances, often within seconds.
In his X post, Adams said the problem has persisted across multiple distribution channels, pointing to earlier periods when fake Uniswap apps circulated while the official app waited for store approvals. He described the recurring pattern as a structural issue in online advertising, arguing that the incentives behind the “ad economy” are enabling repeat abuse.
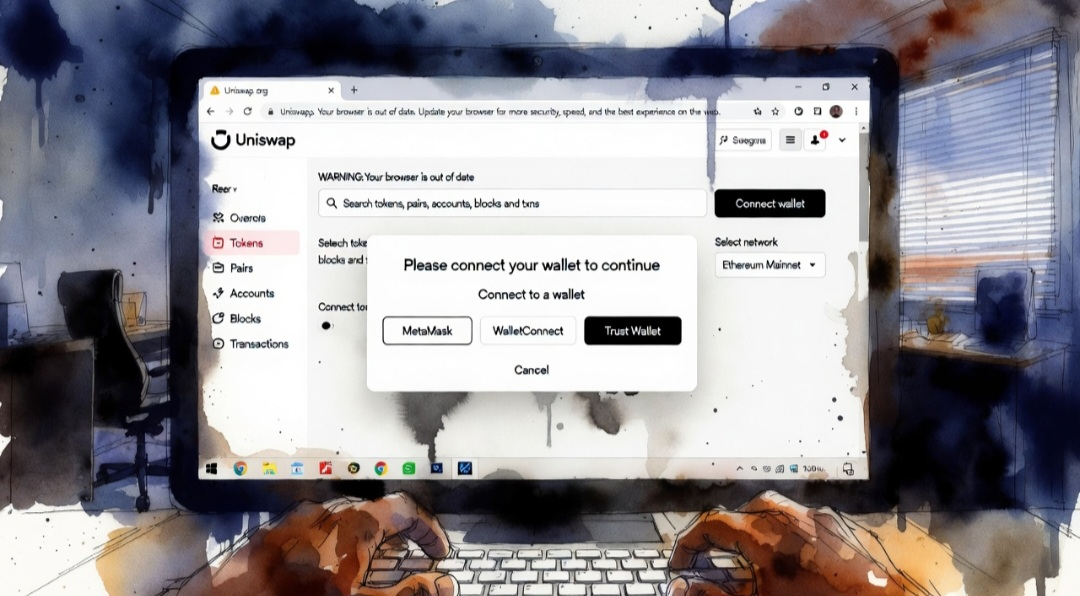
In the February case, the victim shared a screenshot of a sponsored search result that appeared above organic links and routed to an inauthentic Uniswap lookalike. Reports describing the attack said the phishing site copied the real interface closely enough that the key difference was only visible on careful inspection of the URL and subtle UI elements, a tactic designed to pressure users into acting quickly.
The tooling behind these scams is also becoming more standardized. A report describing the same incident said the attacker used a “wallet drainer” kit marketed as a service, and noted that punycode-style domains can be used to make a URL look visually identical by swapping in similar-looking characters. The report also said the drainer referenced in the incident had appeared in other front-end impersonation campaigns.
The renewed warnings are landing against a backdrop of rising scam losses. Blockchain security firm CertiK said cryptocurrency stolen through exploits and scams totaled $370.3 million in January 2026, the highest monthly figure in 11 months and nearly four times higher than January 2025, with one $284 million social-engineering case accounting for most of the month’s value stolen across 40 incidents it tracked.
Adams also pointed to the practical problem that consumer defenses are not always available by default. A separate report summarizing his remarks said some tools used to block malicious ads, including uBlock, have faced bans in certain app stores and browser ecosystems, making it harder for less technical users to filter sponsored results before they click.
Uniswap has been a frequent target for impersonation scams because of its brand recognition and the irreversible nature of on-chain approvals. Unlike a password reset on a centralized service, a malicious approval signed from a wallet can give an attacker immediate permission to move tokens or interact with contracts, and victims often only realize what happened after balances drop.
While Uniswap’s official team can warn users and report fraudulent ads, the recurring pattern underscores that takedowns do not always scale as fast as attackers can rotate domains, buy new ad placements, and re-run the same playbook. Adams’ core message in February was that users should assume sponsored links can be hostile, even when they appear at the top of a mainstream search page.
In a typical sponsored-search phishing flow, attackers purchase ads tied to a protocol’s name so the first result looks like an official landing page. The fake site mirrors the real interface, then prompts a wallet connection and a signature or transaction approval. Once the victim approves, the attacker’s scripts initiate transfers or exploit allowances to drain assets. Reports on the February incident said the victim’s loss was in the hundreds of thousands of dollars, and that the victim publicly attributed it to being fooled by a Google ad rather than a direct compromise of Uniswap itself.
The material on GNcrypto is intended solely for informational use and must not be regarded as financial advice. We make every effort to keep the content accurate and current, but we cannot warrant its precision, completeness, or reliability. GNcrypto does not take responsibility for any mistakes, omissions, or financial losses resulting from reliance on this information. Any actions you take based on this content are done at your own risk. Always conduct independent research and seek guidance from a qualified specialist. For further details, please review our Terms, Privacy Policy and Disclaimers.