Cybercriminals pay up to $20,000 a month for voice-phishing

GK8, a Galaxy subsidiary, has uncovered a growing wave of voice-phishing attacks – phone scams using voice spoofing – aimed at executives at U.S. crypto firms.
On underground forums, researchers found job ads seeking professional voice impersonators (“callers”) and operators ready to follow custom scripts. Pay ranges from per-call fees to monthly contracts exceeding $20,000.
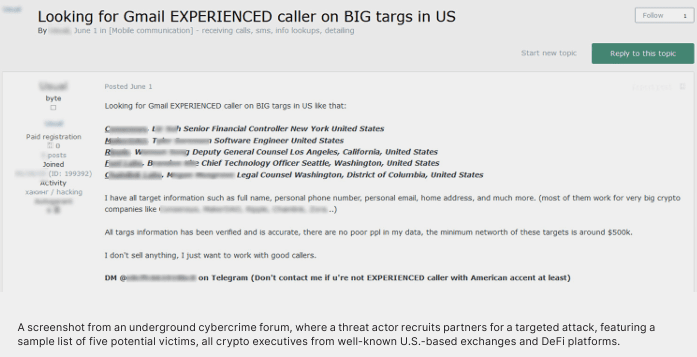

One ad looked for an “experienced caller” to target crypto executives in the U.S. Source: gk8.io
Criminals rely on detailed target datasets: job titles, phone numbers, schedules, financial roles. To cover their tracks, they use VoIP systems, direct inward dialing (DID), and SMS gateways; for realism, they deploy deepfake voices and video.
Targets include CLOs/GCs, CTOs, security engineers, financial controllers, and others with access to keys and custodial systems. According to GK8, the old spray-and-pray model has shifted to “quality over quantity”: fewer targets, more preparation.
While this case focused on the U.S., similar schemes have been reported in Germany, the UK, and Australia.
GK8 recommends treating personal data as potentially compromised, splitting roles and keys (multi-sig), avoiding single-person approval of large transactions, and training staff to spot voice and video security social engineering attempts.
Recommended